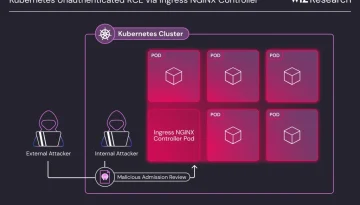
Critical Ingress Nightmare: Unauthenticated Remote Code Execution Vulnerabilities in Kubernetes NGINX Controller Demand Immediate Action
Critical Security Flaws Uncovered in Ingress NGINX Controller: Act Now to Protect Your Kubernetes Clusters. A set of critical security vulnerabilities has been discovered in the Ingress NGINX Controller […]