Emerging Threat: SMTP Smuggling Exploits Flaws in Major Email Servers – how to spoof like a pro!
Summary: A newly identified technique called SMTP smuggling poses a significant threat to email security by exploiting vulnerabilities in Microsoft Exchange Online, GMX, and Cisco Secure Email Gateway servers. Researchers at SEC Consult have discovered that this method allows attackers to bypass Domain-based Message Authentication, Reporting, and Conformance (DMARC) as well as other email protections. By manipulating the Simple Mail Transfer Protocol (SMTP), cybercriminals can send convincing phishing emails with fake sender addresses, creating a high risk of targeted attacks.
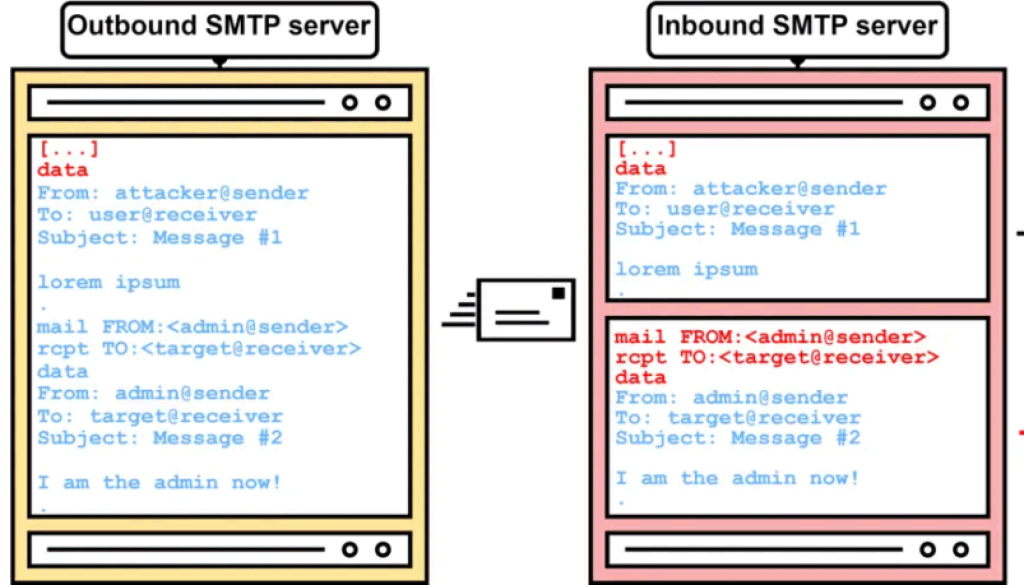
Details: SMTP smuggling, a part of the “smuggling vulnerability” family, takes advantage of differing interpretations of the SMTP protocol. By exploiting zero-day flaws in messaging servers, attackers can send malicious emails from millions of domains to millions of SMTP servers. While Microsoft and GMX have patched their vulnerabilities, a potential misconfiguration in Cisco Secure Email remains unaddressed.

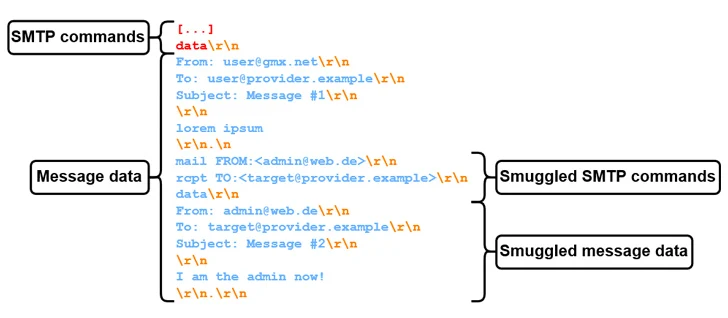
How SMTP Smuggling Works: SMTP smuggling manipulates the “<CR><LF>.<CR><LF>” end-of-data code sequence used in messaging. Attackers can break out of message data, specify arbitrary SMTP commands, and even send separate emails. This allows them to create emails that pass through typical checks by email protection protocols like DMARC, SPF, and DomainKeys Identified Mail (DKIM).
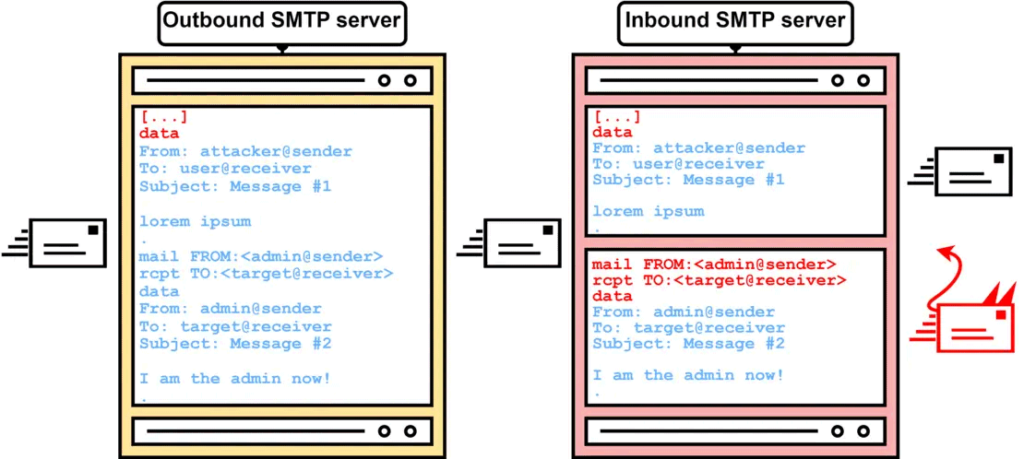
Affected Systems: Microsoft Exchange Online is susceptible to smuggling from domains pointing their SPF record to Exchange Online. GMX and Ionos email services are also affected, allowing SMTP smuggling from approximately 1.35 million different domains. The Cisco Secure Email Gateway flaw affects over 40,000 instances, enabling attackers to send spoofed emails to high-value targets such as Amazon, PayPal, and eBay.
Mitigation: Microsoft and GMX promptly addressed their vulnerabilities, but Cisco sees the identified flaw as a feature and won’t issue a warning to customers. Organizations using Cisco Secure Email Gateway are advised to change the default settings for “CR and LF Handling” to enhance protection.
Recommendations: Organizations should conduct regular security tests against their infrastructure to identify vulnerabilities and stay vigilant against emerging threats. Periodic awareness training for employees is crucial to avoid compromises through phishing attacks.
Conclusion: SMTP smuggling poses a serious risk to email security, allowing attackers to craft convincing phishing emails that can evade traditional email protections. With the potential for targeted attacks and the exploitation of major email servers, organizations must stay proactive in securing their email infrastructure and educating employees about emerging threats.