Critical Security Flaw Uncovered in ChatGPT Atlas Browser: What Users Need to Know
OpenAI’s newly launched ChatGPT Atlas browser is facing intense scrutiny after cybersecurity researchers discovered alarming vulnerabilities that could expose users to unprecedented security risks. Just days after its October 21, […]

Cut Cloud Costs by 40% Without Breaking Your Infrastructure: 2025 Guide
Your AWS bill just doubled again—and nobody can explain why. If you’re an IT manager or DevOps engineer at a mid-size company, you know the pain: rising cloud costs that […]
OpenAI Just Declared War on Google Chrome: Why Atlas Could Change Everything
The internet’s future was rewritten this week. OpenAI’s new “Atlas” browser isn’t just another Chrome alternative—it’s a direct assault on Google’s 20-year stranglehold on how we access the web, and […]

AI Agents vs. Cyber Threats: How Autonomous Security Is Winning the War
In 2025, cyberattacks are faster and more sophisticated than ever. But now, a new generation of AI agents is fighting back—automatically predicting, blocking, and even fixing threats before human teams […]

Vulnerability Management in 2025: From Swamped to Secure
Cyber attackers don’t wait—neither can your team. Vulnerability management has entered a new era, where rapid patching, risk-based prioritization, and automation separate the secure from the vulnerable. Here’s how to […]
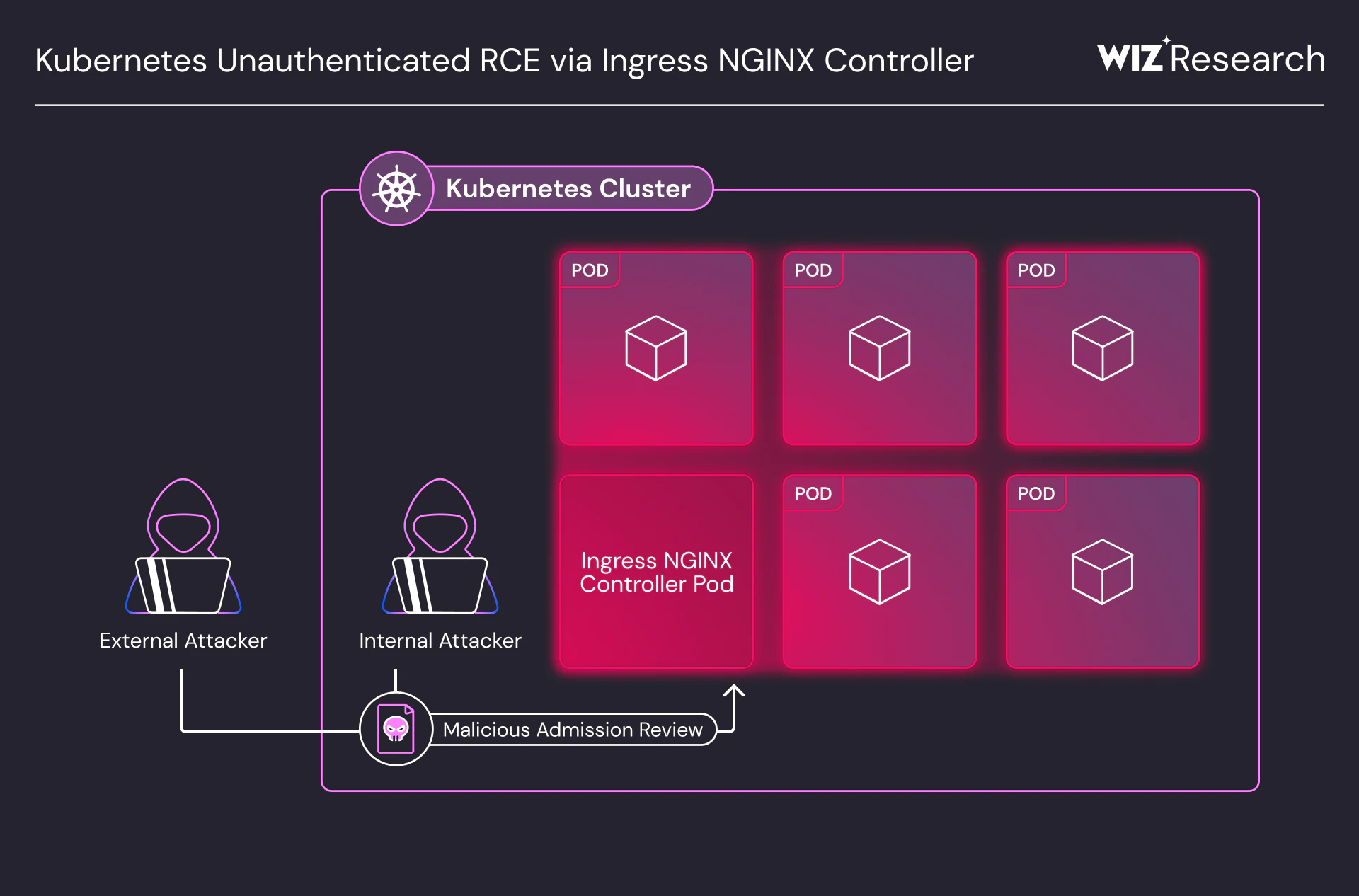
Critical Ingress Nightmare: Unauthenticated Remote Code Execution Vulnerabilities in Kubernetes NGINX Controller Demand Immediate Action
Critical Security Flaws Uncovered in Ingress NGINX Controller: Act Now to Protect Your Kubernetes Clusters. A set of critical security vulnerabilities has been discovered in the Ingress NGINX Controller […]

Apache Tomcat CVE-2025-24813: Understanding and Mitigating the Remote Code Execution Threat
Introduction: A serious vulnerability, identified as CVE-2025-24813, has been disclosed in Apache Tomcat, a widely used web server software. This unauthenticated remote code execution (RCE) flaw within Tomcat’s partial PUT […]

Linux Maintainers Infected by SSH-Dwelling Backdoor: A Two-Year Compromise
Introduction In a shocking revelation, it has been disclosed that the infrastructure used to maintain and distribute the Linux operating system kernel was compromised for two years by sophisticated malware. […]